Why Everyone Should Have an Encrypted System DiskHow to Encrypt Your Entire System Disk Using TrueCryptHow to Permanently Decrypt Your System Disk
Why Everyone Should Have an Encrypted System Disk
Okay, let me qualify this. Not everyone should encrypt their system disk. Just everyone who has personal or financial information on their computer, such as tax returns, stored passwords, browsing history, emails, resumes, address books, photos and videos, utility bills, account histories, etc. If all you use your computer for is reading Reddit in Incognito Mode, then you probably don’t need to encrypt your data. But if you are like the vast majority of personal or business computer users, you have valuable data that warrants protection. Here are the top three risks associated with having an unencrypted hard drive.
1. Thieves aren’t just after your hardware
“Ah, but I have my Windows account password-protected. He won’t even be able to log on,” you say. Sorry. Data/laptop thieves only need to be a little bit clever in order to bypass the Windows login screen and get at your data. At the bare minimum, all he’d need is a bootable installation of Linux on a thumbdrive and he could boot up your computer and explore the contents of your system drive in its entirety. This is because your Windows password protection only prevents someone from logging in to your Windows user account. It doesn’t stop them from accessing the data by another means anymore than an ignition key stops a carjacker from breaking your window and hotwiring your car. There are edge cases I know. Perhaps you encrypted your files and folders using Steve’s EFS Encryption trick for Windows however my guess is, that’s indeed the exception not the rule. Let’s move on.
2. For sale: your old hard drive (and all of your data)
Warranties are fantastic. I’ve had hard drives, power sources and entire computers replaced under warranty lickety split, free of charge, no hassle. But when it comes to hard drives, there’s a catch. In order to get a repair or replacement, you have to mail your old hard drive in (RMA process). The same goes for sending in your entire computer for warranty repairs. Before doing this, it seems logical to securely erase any sensitive data from your hard drive, just like you would before selling or recycling your computer. But if your computer is bricked or your hard drive won’t even mount , then that’s not an option. You’re going to have to send in your hard drive with all of your data still intact. This would be problematic if, say, there was an unscrupulous technician (perhaps a 3rd party subcontractor) harvesting customer data whilst performing warranty service. That’s probably rare however it does happen. But what is far more common is the practice of reselling used drives. If you’ve been keeping an eye on the deal sites, you may have noticed “refurbished” hard drives for sale at a big discount. These refurbished or recertified hard drives are usually drives that have been returned or exchanged under warranty. Oftentimes, rather than making you wait while they evaluate and repair your hard drive, manufacturers will send you a brand new hard drive to cover your warranty. Then, they’ll take your drive, fix it up, reformat it and (maybe) securely wipe it before repacking it and selling it back to another customer. While most everyday users won’t even know to look for residual data on a used drive, a determined data recovery guru or… even a bored kid could likely glean just enough data from a reformatted drive to do some damage using simple to use free tools available on the net. A Social Security number, after all, is only nine digits long – every time if you know what I mean. If you are returning hardware, it’s a good idea to ask the vendor or manufacturer to destroy it after they’ve completed their evaluation. But as one gentleman returning a computer to Best Buy discovered, making the store follow through on its promises isn’t always easy. As chronicled by MSNBC blogger Bob Sullivan, a Cincinnati customer returned his broken computer to Best Buy, thinking his old hard drive would be drilled and disposed of in a secure manner. Much to his chagrin, he received a phone call six months later from a stranger who told him “I just bought your hard drive” at a flea market in Chicago. Ouch….
3. Throwing out a hard drive? That could be a federal offense
FACTA, HIPAA and other federal privacy and identity theft prevention regulations require businesses to properly dispose of customer and patient records. Paper records—manila folders, medical charts, loan applications—are the first thing to come to mind. But digital records are also covered by federal law. If you’re a business, that puts you on the hook for properly disposing of your hard drives and other media. These days, most institutions go far beyond drilling holes through the platter and instead shred the drives into tiny chunks, just like paper; or they outsource the job to a company who specializes in this providing certificates of destruction to prove the work was completed. But if you’re not a business or hospital, there’s no need to worry, right? Not exactly. Let’s say you hire a babysitter or a nanny. As part of your due diligence, you order a background check on her and save the results—including her address history, her SSN, etc.—onto the hard drive of an old computer. Years later, you donate the old computer to Goodwill, some college kid buys it, does a file undelete or data recovery and bam — has way more information about your nanny than he legally should. As your nanny’s employer, you’ve failed in your federally-mandated duty to protect her identity.
System Disk Encryption to the Rescue
The real liability in all of these situations is letting sensitive or confidential information reside unencrypted on a hard drive. Data is notoriously difficult to eradicate. This is especially true when we’re talking about solid-state drives (SSDs) and flash-based media (like SD cards); one study found that it is nearly impossible to delete data on SSDs. That’s why encryption is such a graceful solution. With encrypted data, it doesn’t matter nearly as much if your data falls into the wrong hands. Unless they can crack the encryption or guess your password, they aren’t going to get any usable personal information from your disk. If a data thief mounts your disk to another system, all they will find is encrypted gibberish. Combine encryption with a secure format (when possible), and you are all but invulnerable to data theft. System disk encryption is convenient because it doesn’t disrupt your normal computer usage, except for an extra password to enter at boot up and a slight drop in performance. TomsHardware deemed the performance impact “not noticeable” to average users. System disk encryption protects every bit of data on your hard drive without requiring you to pick and choose which documents and files to encrypt. And best of all, you can do it for free using TrueCrypt. Here’s how:
Encrypt Your Entire System Disk Using TrueCrypt
Download and install TrueCrypt on the Windows machine that you want to encrypt (this tutorial uses TrueCrypt 7.1a). Then, launch TrueCrypt and click System | Encrypt System Partition/Drive…
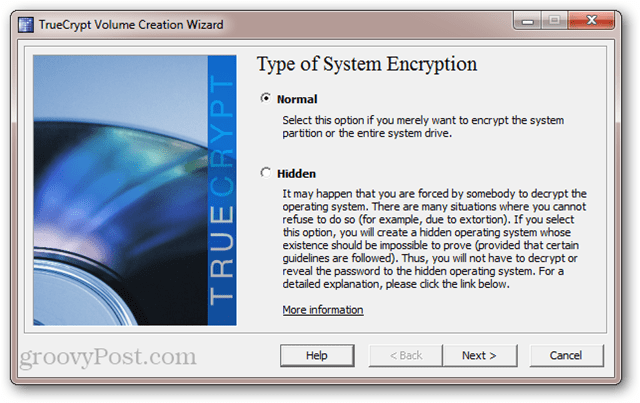
Next, select the type of system encryption. I recommend choosing Normal for now. Hidden is probably a bit overkill (read the description in the screenshot to learn about its intent). Click Next.
In the Area to Encrypt window, you have two options. If you have your data and your Windows installation on the same partition, then choose the first option (“Encrypt the Windows system partition”). If you have multiple partitions—e.g. one for your data and one for your operating system—then choose the second option (“Encrypt the whole drive”). If you are unsure, go with the second one. Click Next.
In the next screen, choose Single-boot or Multi-boot and click Next.
Next, choose your encryption options. If you don’t know what any of this means, then the default settings are good enough for you. Note that you do have the option to use multiple levels of encryption. While this is more secure, it does increase the performance impact (that is, your computer will run slightly slower than if you chose a single level of encryption). Click Next.
Choose a password. As always, longer passwords are stronger. But make sure it’s one you can remember. Click Next.
Move your mouse cursor to randomize the pool content. Click Next.
View your master and header keys. You don’t have to write this down or anything. This is just FYI. Click Next.
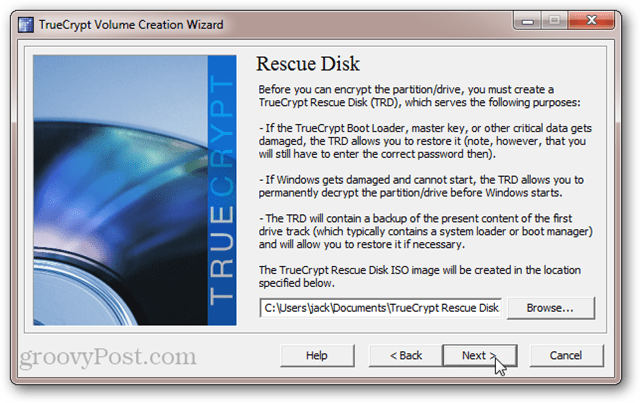
TrueCrypt will now prompt you to burn a TrueCrypt Rescue Disk. Do not skip this step. TrueCrypt uses a special boot loader to decrypt your drive. If your system becomes damaged or corrupted, then you will need this disk in order to access your data. So don’t lose it. Note also that the TrueCrypt Recovery Disk is specific to your encrypted system disk. You can’t use a rescue disk that you created for another encrypted disk. Click Next to start the process.
If you don’t have an CD/DVD drive on your computer, you can also create the TrueCrypt Recovery Disk on a USB drive. If you have a burner on your computer, you’ll be taken directly to the Windows Disc Image Burner utility and you won’t see the prompt below.
After burning your TrueCrypt Rescue Disk, you’ll be asked if you want to choose a secure wipe mode. Again, this is for the ultraparanoid. You can probably skip this step and be okay. But if you have a very large drive that you’ve been using for awhile, it won’t hurt to wipe the drive before encrypting it. The only thing you have to lose is time. But if you aren’t worried about someone using magnetic force microscopy to recover your overwritten data, choose None (fastest) and click Next.
TrueCrypt will now run a system encryption pretest. This entails a reboot and a prompt for your new password. This ensures that the TrueCrypt Boot Loader was installed correctly and that everything works fine before your drive is encrypted. Click Test when you are ready. You’ll still have an opportunity to back out if the test doesn’t go well.
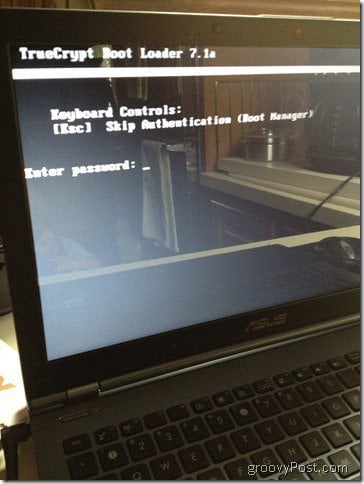
After clicking Test, you’ll be prompted to reboot. Upon doing so, you’ll see your normal BIOS screen followed by the TrueCrypt Boot Loader. Enter your password to finish booting into Windows.
After a successful pretest, you can click Encrypt to finish the job.
Depending on the size of the volume and the speed of your computer, this could take awhile. On my Core i5 laptop, it took about five hours to encrypt my 250 GB system disk (I let it run overnight). On my AMD Phenom II X4 2.8 Ghz desktop, it estimated 18 hours to encrypt my 1.5 TB hard drive. Your mileage will vary.
Fortunately, you can defer or pause the encryption process at any time. You can even restart or shut down your computer and resume the encryption process where you left off. TrueCrypt will run the encryption process in the background while you use other applications, but this will lengthen the overall time it takes to encrypt. When the encryption is complete, your Windows system will look and feel exactly the same as it did. The only difference is that you’ll see the TrueCrypt Boot Loader screen every time you power on your computer or wake it from hibernation. You won’t have to enter your pre-boot authentication password after waking from sleep.
Undoing an Entire System Disk Encryption
If you’re tired of punching in an additional password or if you want to permanently decrypt your system disk for some other reason, you can undo your TrueCrypt system disk encryption by clicking System > Permanently Decrypt System Partition/Drive.
You’ll be given due warning that your drive will be unencrypted afterward. After clicking Yes the requisite number of times, the decryption process will begin. Settle in—this will take nearly as long as it took to encrypt the drive in the first place. Again, you can use your computer and/or pause or defer the decryption at any time.
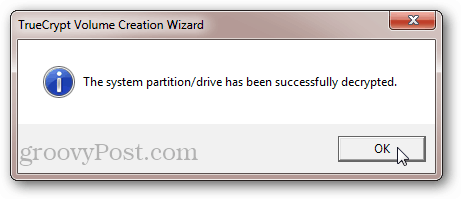
After the decryption is complete, you’ll be asked to reboot. The TrueCrypt Boot Loader screen won’t appear anymore and your system disk will be unencrypted.
Note that even though you won’t be prompted to enter your password, the TrueCrypt Boot Loader will still be installed on your system disk. This shouldn’t present any problems. But if it bugs you knowing that there is residual stuff leftover on your master boot record, you can rewrite your MBR using a Windows 7 Installation disc or a Windows 7 System Repair Disc.
Conclusion
Encrypting your system disk with TrueCrypt is free, secure and easy. There’s relatively little overhead in terms of performance impact and added inconvenience. But the benefits to your data security are immense. In this way, system disk encryption is a lot like home insurance. Hopefully, you’ll never have to use it. But when the unthinkable happens, you’ll be glad as hell that it’s there.
I use Dropbox, and it makes no difference on an encrypted system disk. Of course, my data in Dropbox is not encrypted with this setup. If you were to sync an encrypted volume (see: https://www.groovypost.com/howto/howto/secure-encrypt-dropbox-folder-account-contents/), then you would not be able to access your files from another device that didn’t have TrueCrypt installed. Large size neodymium magnets. Like this one Short answer: yes — you have to decrypt your drive before upgrading. But the thing to consider is that, although the files you are specifically trying to secure are kept safe in the encrypted partition, there may be some trace data that could potentially be recovered by someone who obtains your hard drive after you’ve sold it or discarded it. For example, if you mount a partition and then open a sensitive Word document that’s stored in the partition, Windows will still put the temporary file for that somewhere in the (unencrypted) system disk. These temp files are SUPPOSED to be cleaned up, but that doesn’t always happen. And then there’s the matter of your browsing history, cached form data, passwords, etc. If you had encrypted your entire system disk, this wouldn’t be a problem, since the temp files would also be encrypted. The only way a thief could get into your stuff is by accessing your computer after you’ve already booted it up. So, about your question: was that a good alternative? Certainly. I think it’s a great idea. But it’s not as strong as encrypting your entire system disk. As an extra precaution, I might recommend doing a secure format of your entire drive before discarding or selling your computer. See: https://www.groovypost.com/howto/4-ways-secure-format-hard-disk-drive/ Eraser, which is mentioned in that article, can securely delete individual files. There’s also another (not free) program called R-Wipe and Clean that’s supposed to sniff out residual and temp data and securely wipe it. You might want to look into that. [Full disclosure: I do some freelance writing for the makers of R-Wipe and Clean, but from what I know about the product, it seems pretty good.] ANYTHING! ;) F u t u r e The following features are planned to be implemented in future versions: Full support for Windows 8 Ability to encrypt Windows system partitions/drives on UEFI-based computers (GPT) Command line options for volume creation (already implemented in Linux and Mac OS X versions) ‘Raw’ CD/DVD volumes and more. Any info here greatly appreciated. Thanks. Encrypting your hard drive should be layered with the normal Windows security features. If you want to password protect your computer when it is asleep, you should enable password protection on wakeup. Go to Control Panel -> Power Options -> Require a Password on wakeup (left-hand pane). So, this protects you in two ways:
- It protects your hard drive from being mounted without your decryption key (e.g. removing the hard drive and mounting it on another machine, thereby bypassing the windows logon process)
- It protects your hard drive from being accessed once it’s already been mounted (e.g. when the computer is in sleep mode). The only way someone would be able to hack your computer is to guess your password. Because if they removed the hard drive from your computer, it would be unmounted, and therefore you’d be protected by #1. But, are there any full disk encryption apps for non-Samsung Android devices? All I have seen will encrypt files or pics. Comment Name * Email *
Δ Save my name and email and send me emails as new comments are made to this post.